Our Solutions for Law Enforcement

Forensic Data Center is the Ultimate solution of Network forensic, works in a series of processing and imaging computer connected and integrated directly with a hi-speed, hi-capacity server to share resources. The file server operates as the core of the Forensic data center and can be used as a central storage facility for Forensic Images as well as applications software for use by the client processing and imaging stations.

It’s a high performance data recovery and crime scene investigation workstation. Core Forensic Applications runs here. Simply remove the hard drive(s) from the suspect system and plug them into Forensic Workstations and acquire the digital evidence. Forensic Workstations will acquire data directly from IDE/EIDE/ATA/SATA/ATAPI/SAS/Firewire/USB hard drives and storage devices and save forensic images to Blu-Ray, DVD, CD or hard drives. These systems also acquire data from Blu-Ray, CD-ROM, DVD-ROM, Compact Flash, Micro Drives, Smart Media, Memory Stick, Memory Stick Pro, xD Cards, Secure Digital Media and Multimedia Cards.

It is a Military Class Rugged kit which includes a high configured Laptop with Core forensic application, a full assortment of forensic write blockers, the speed and flexibility of the TD1 forensic duplicator, and all the cables, adapters, and extras one would need to complete the forensic process anywhere in the world. Whether in the field or in the office this kit provides an investigator with, in essence, a digital forensic lab in a portable case. The kit is completely housed in a practically sized, weatherproof, travel case that conforms to all airline baggage standards.

This solution can recover data that is logically damaged from all the main hard drive vendors such as: Seagate, Samsung, Hitachi, WD, Fujitsu, Maxtor, Toshiba, IBM and more. And in terms of Physical Damage, if your Hard drive is physically damaged then this solution could be a idle for • Burned hard drive data recovery • Water and other liquid damaged hard drive data recovery • Dropped Laptop and Hard Drive Data Recovery • Data recovery from power failure in hard drive due to light fluctuate • Data recovery from clicking sound in hard drive • Data recovery from overheating hard drives / PCB problems
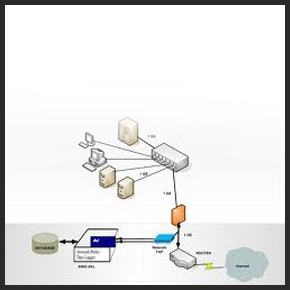
Operating like a network surveillance camera, it allows you to monitor, capture, analyze and graphically visualize network traffic to see exactly what is happening on your network during a proactive audit or cyber investigation. By watching network communications from a high-level, patterns and communication paths will be uncovered that allow you to zero in on suspicious activity, such as policy violations, internal collusion, bandwidth overuse, and questionable in- or outbound connections. Furthermore the visibility gained by using it enables you to clearly determine the scope and scale of a security breach, as well as proactively identify weaknesses in your security configurations. In addition, you can play back events from thousands of communications to validate a threat and perform root cause analysis. It dramatically enhances your incident detection and response capabilities, giving you the power to see what your signature-based tools cannot.

• Thorough extraction of mobile phone data, including contacts, SMS messages, photos, videos, call logs, audio files, ESN, IMEI, ICCID, IMSI and more • Unrivalled coverage and compatibility, with support for more than 3000 phones • Mapping of geo-tags on Google Maps • SIM ID cloning circumvents missing SIM card and PIN-locked SIMs and neutralizes the phone from any network activity during analysis • Field-ready mobile forensics – portable, fast and easy to operate, this Ruggedized Kit is battery powered and comes with all accessories needed for harsh field conditions

High-performance distributed password recovery for forensic and government agencies, password recovery and data recovery services and corporations. Recover the most complex passwords and strong encryption keys in realistic timeframes. Accelerate the recovery by offloading calculations to NVIDIA and ATI GPUs and scale to over 10,000 workstations with zero scalability overhead. We are introducing the first ever commercial SUPER COMPUTER for this solution.

This solution can support almost all browsers, email clients and chat engines. It craves data from history and live ram to investigate the contents to investigate the cyber crime.

Porn Detection kit is a thumb drive device that will search through all the images on your computer, scan them for pornographic content, and create a report of suspected pornographic images. It even scans deleted images and Internet cache files so there's no hiding Internet activity. This means even if Internet Explorer cache files are deleted, many images can still be recovered and scanned for pornography. Best of all, no software is installed on the target machine so they don't know you've performed a search. You can even securely delete objectionable images. Protect your computer from unwanted pornography. Someone doesn't have to be seeking out pornographic images to contaminate your computer. In fact, many porn sites contain harmful viruses that can do more damage. The Porn Detection Stick offers you peace of mind that your system is clean of unwanted illicit or even illegal images.

Its is a portable kit which contains a complete family of hardware write blockers along with adapters and connectors for use in acquiring a forensically sound image of virtually any hard drive or storage device you may encounter. Simply select the appropriate Write Protected UltraBlock and attach it to the source drive and use your desktop or laptop to acquire a forensically protected disk image to an internal drive or externally connected drive enclosure.
Our Solutions for Government

It will built on a Highly configured Forensic Workstation which is a court-accepted digital investigations platform that is built for speed, analytics and enterprise-class scalability. Known for its intuitive interface, email analysis, customizable data views and stability, it lays the framework for seamless expansion, so your computer forensics solution can grow with your organization’s needs. Its also includes a malware triage technology that is available as an add-on. The first step towards automated reverse engineering, it provides threat scores and disassembly analysis to determine both the behavior and intent of suspect binaries. View data in multiple display formats, including timelines, cluster graphs, pie charts and more. Quickly determine relationships in the data, find key pieces of information, and generate reports that are easily consumed by attorneys, CIOs or other investigators.

Evidence Center helps forensics and criminal investigators to search, extract, analyze and export various user online activities like chats made with Instant Messengers, sites visited with Internet Browsers and e-mail sent with desktop e-mail clients. The tool has clear and intuitive user interface. Very much effective tool for monitoring the insider threat. Actually most of the organizations are in the need of this solution. Evidence Center helped many businesses prevent security breaches, discover fraud and theft of intellectual property, and combat employee misconduct. • Discovers more evidence than competition • Analyzes IM/chat histories, P2P transfers and file sharing • Prevent IP theft, combat fraud and employee misconduct • Thorough analysis discovers hidden and destroyed evidence • Simple by design; feasible for single incidents • Clean and concise reports can be presented as court evidence
Our Digital Forensic Accessories

Connect your Mac Air BLADE Type SSD (128Gb or 256Gb) to a SATA power and data cable. Pentalobe screwdrivers are also available to disassemble your iPhone or MacBook Air.

Easily connect your 1.8 inch Mac Air SATA LIF hard drive to a SATA cable. Each adapter features a SATA LIF female drive interface, 2 interchangeable SATA LIF connector cables, and a and convenient carrying case.

Includes 2" IDE Cable, 2.5" hard drive adapter, 1.8" pin Hard Drive Adapter, MicroSATA Adapter and ZIF Adapter in zippered case.

The MultiDrive Adapter is designed to be used with various write blockers including the UltraBlock IDE, UltraBlock IDE/SATA, FireFly IDE and the UltraBay. The MultiDrive Adapter supports standard 2.5 inch IDE hard drives, 1.8 inch IDE hard drives with 50 pin connector, Toshiba ZIF hard drives, Samsung ZIF hard drives, Hitachi ZIF hard drives and other hard drives with a 40-pin ZIF connector.

This kit is offered by Digital Intelligence to meet the high duty cycle required for Forensic applications. Rugged pocket size enclosure with structurally mounted power connection. Easily connect your 1.8 inch notebook IDE hard drive to a 40-pin IDE cable. Each adapter features a ZIF female laptop drive interface, 4 interchangeable ZIF connector cables, and a and convenient carrying case.

The 1.8" HD enclosure connects to either a ZIF or PIN drive. The enclosure operates at USB 2.0 speeds and requires no additional power supply. Available with or without a hard drive pre-installed.

The 2.5" HD enclosure connects to a SATA drive. The enclosure operates at USB 3.0 speeds and requires no additional power supply.

This enclosure holds a single 3.5 inch SATA Hard Drive and uniquely supports all of the following interfaces: eSATA, FireWire 400 (1394a), FireWire 800 (1394b), and USB 2.0.

Connect and copy USB devices on your Forensic Duplicator.

Connect and copy SAS hard drives on your Forensic Duplicator.

Connect and copy USB and SAS hard drives on your Forensic Duplicator.

Modular Storage Systems have been designed specifically for the needs of the computer forensics community and meet the storage requirements. All-in-one integrated and versatile individual modules are now available.

Fernico FAR systems are specifically designed for Digital Forensic Investigators who need a complete solution for backup, restoration and acquisition of forensic data evidence. Backup Digital Evidence Automatically to DVD, HD-DVD or Blu-Ray Disc. Restore Disks to Rebuild or Review Cases. Acquire Evidence From a Variety of Media.

Replacement Forensic Duplicator 2 power supply and power cord.

Replacement Forensic Duplicator and Modular Device power supply and power cord.

Replacement UltraBlock and FireFly power supply and power cord.





